The $550,000 Question Every Maritime SMB Operator Is Asking about IMO 2021
“We thought we were doing everything right,” the IT Director of a 12-vessel regional container operator told me last month. “We had basic firewalls, antivirus software, regular password updates. Then one morning, I got the call that ransomware had spread from our shore office to three of our vessels through what should have been a secure connection.“
This operator isn’t alone. In 202, according to Marpoint, cyberattacks cost the maritime industry approximately $550,000 per incident on average, up dramatically from $182,000 in 2022. For small and medium-sized maritime operators, a single successful attack can represent months of profit or even force them out of business entirely.
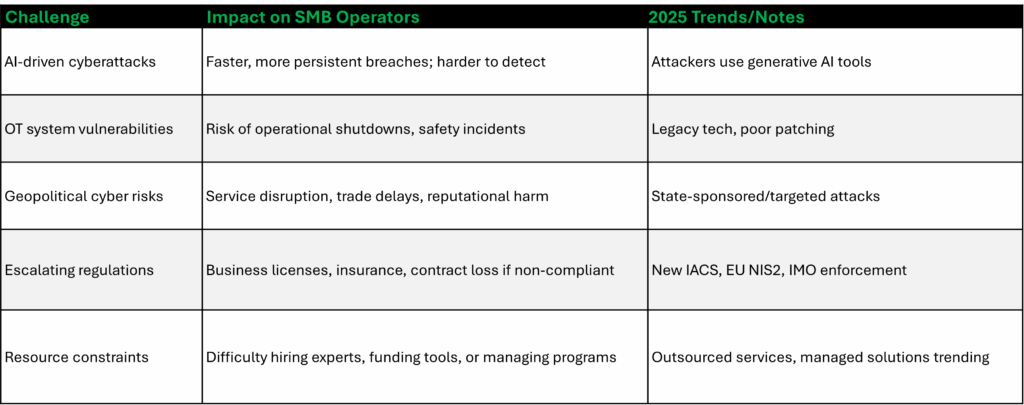
The harsh reality is that IMO 2021 compliance isn’t just about ticking regulatory boxes anymore. The maritime industry in 2025 faces unprecedented cybersecurity challenges, from AI-driven attacks and OT vulnerabilities to geopolitical cyber conflicts. Compliance has become a business survival issue, but the path forward seems impossibly complex.
Here’s why most guidance fails SMB operators, and the one critical fix that actually works.
1. Why standard IMO 2021 advice doesn’t work for small fleet operators
The fundamental problem with most IMO 2021 compliance guidance is that it’s designed for major shipping lines with sizable IT departments, decicated cybersecurity specialist, millions+ budgets, and purpose-built systems. SMB operators face a completely different reality.
1.1 The SMB maritime operator’s compliance nightmare
Most SMB operators run on a patchwork of systems installed over many years. Your ECDIS might be from 2018, your engine monitoring from 2015, and your fleet management software from 2020. Each system was installed when cybersecurity was not a priority, and now you’re supposed to somehow integrate them into a coherent cyber risk management framework.
Unlike shore-based businesses, your critical operations happen hundreds of miles from your IT support. When a cyber incident occurs at sea, you can’t simply walk over to restart a server or isolate a compromised device. Yet most cybersecurity advice assumes immediate physical access to all systems.
You’re operating with a small IT staff who also handles everything from email problems to navigation system updates. The idea of implementing comprehensive cybersecurity monitoring across multiple vessels while maintaining day-to-day operations feels impossible.
Non-compliance with IMO Resolution MSC.428(98) may result in regulatory penalties, but what does compliance actually look like during an audit? Most guidance provides high-level frameworks without explaining what auditors specifically look for or how to demonstrate compliance in practical terms.
1.2 The one critical thing that makes a difference: Network Segmentation
After reviewing hundreds of reported maritime cybersecurity incidents, including cases highlighted in the US Coast Guard’s 2024 CTIME report, one pattern is consistently evident: the connection between shoreside corporate networks and shipboard systems is the principal breach point in real-world attacks.
“The majority of ransomware impacting marine operations originates with networks or services exposed through the corporate/shoreside environment, then propagates to vessel systems where segmentation is weak.”
2024 US Coast Guard CTIME report
The 2024 Coast Guard CTIME report detailed the first incident where ransomware breached a vessel’s shipboard network in the encryption phase. Attackers initially exploited weak corporate VPN credentials, then pivoted through unpatched corporate backup servers to access the vessel environment. Because ship and shoreside networks were connected, ransomware rapidly encrypted shipboard servers as well as shoreside systems.
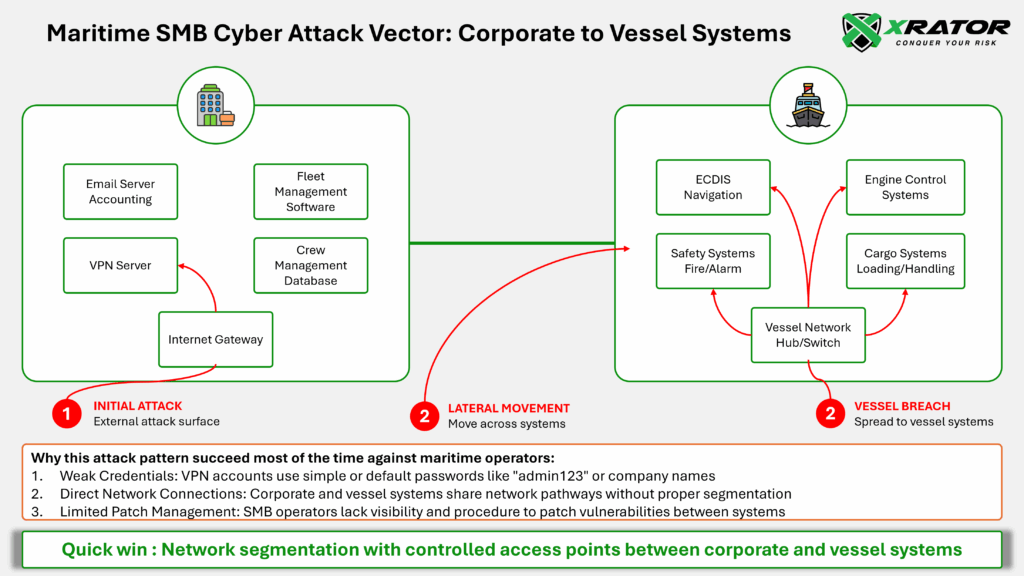
Analysis of recent cases shows this common attack pattern:
The initial compromise almost always begins in the corporate network (typically via phishing, credential brute-forcing, or exploiting remote services).
Attackers gain administrator priviledges and move laterally through poorly segmented networks.
Once inside, they leverage trust relationships and remote management tools to reach vessel systems, particularly when segmentation is weak or remote access is required for operational control and logistics
Don’t let your budget dictates your cyber insecurity: get a free external attack surface assessment for your systems.
Network segmentation, properly isolating your vessel operational technology (OT) systems from your corporate information technology (IT) networks, is the first and most effective cyber compliance measure you can implement.
1.3 Diagnose of a MSC.428(98) failure
As cyber expert, we can see that most cybersecurity advice misses the mark because it doesn’t address the real user experience of SMB maritime operators. Before diving into solutions, let’s understand why traditional approaches fail.
Your typical business involves managing vessel schedules, handling crew changes, coordinating with ports, managing fuel procurement, and dealing with regulatory requirements. Cybersecurity can’t be a separate, complex process : it needs to integrate seamlessly into these existing workflows.
SMBs operates under constraints that major shipping lines don’t face: limited shore-side IT support, mixed-generation equipment, tight operational budgets, and remote operational environments. Solutions must work within these constraints, not ignore them.
The deepest frustration isn’t understanding how to implement cybersecurity measures, it’s knowing exactly what is important to demonstrate compliance during an audit without disrupting operations or breaking the budget.
2. The 5-Step network segmentation starter kit for maritime operations
Based on the IMO’s Identify, Protect, Detect, Respond, and Recover framework, here’s a practical approach specifically designed for SMB maritime operators focusing on the critical network segmentation challenge.
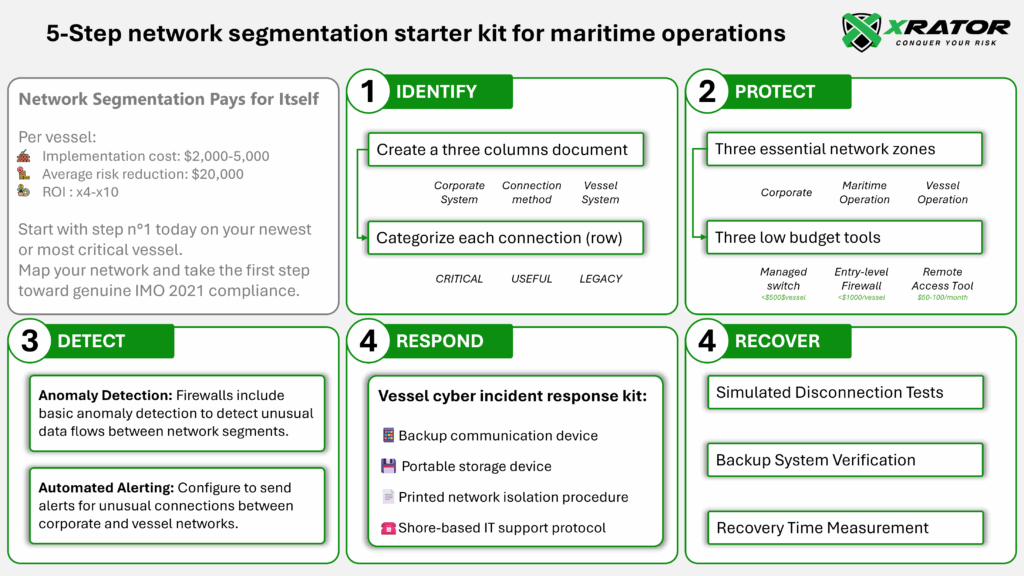
2.1 IDENTIFY – Map your network reality
Don’t try to create complex network diagrams. Focus on answering three critical questions:
- Which vessel systems can currently access your shore-based corporate network?
- Which shore-based systems can currently access vessel operational systems?
- Where are the connection points that could allow malware to spread between corporate and vessel networks?
Practical Implementation
Create a simple three-column document: Corporate Systems, Connection Method, Vessel Systems. For each row, note whether the connection is essential for operations, useful but not critical, or legacy connectivity that serves no current purpose.
Real-World Example
A regional ferry operator discovered they had 47 different connection points between shore and vessel systems, but only 12 were actually necessary for daily operations. Eliminating the unnecessary connections reduced their attack surface by 74% without affecting operations.
2.2 PROTECT – Implement basic segmentation
You don’t need enterprise-grade network equipment. Focus on creating three distinct network zones:
- Corporate Zone: Office systems, email, accounting, administrative functions
- Maritime Operations Zone: Fleet management, voyage planning, crew management
- Vessel Operations Zone: Navigation systems, engine monitoring, safety systems
Practical Tools for SMB Operators
Most SMB operators can achieve effective segmentation using:
- Managed switches with VLAN capability: Netgear or Cisco small business lines (under $500 per vessel)
- Firewall appliances: SonicWall or Fortinet entry-level models (under $1,000 per vessel)
- Remote access solutions: TeamViewer Business or similar with two-factor authentication
Implementation Priority
Start with your newest or most critical vessel. Success on one vessel provides a template for fleet-wide implementation and demonstrates ROI to justify additional investment.
2.3 DETECT – Set up monitoring that works at sea
The SMB Reality of Monitoring You can’t implement 24/7 security operations centers, but you can set up automated monitoring that works with intermittent connectivity and limited technical support.
Practical Monitoring Solutions
- Network traffic anomaly detection: Many modern firewalls include basic anomaly detection that can identify unusual data flows between network segments
- Automated alerting: Configure systems to send alerts when unusual connections are attempted between corporate and vessel networks
- Daily connectivity reports: Simple automated reports showing which systems accessed which networks can help identify potential issues
Key Monitoring Metrics for SMB Operators
Focus on three critical indicators:
- Unusual data transfers between corporate and vessel networks
- Login attempts to vessel systems from unexpected locations
- Changes to network configurations or security settings
2.4 RESPOND – Create response procedures for remote operations
When a cyber incident occurs at sea, your response procedures must work without immediate technical support or physical access to systems.
Practical Response Procedures
Develop simple, step-by-step procedures that bridge crew can follow:
- Network isolation procedures: Simple steps to isolate vessel networks from corporate systems
- Essential systems priority: Clear list of which systems must remain operational for safety
- Communication protocols: Secure methods for vessel-to-shore communication during incidents
Pre-positioned Response Tools
Each vessel should have a “cyber incident response kit” including:
- Backup communication device (satellite phone or separate internet connection)
- Portable storage device with critical system recovery files
- Printed procedures for network isolation and essential system operations
- Contact information for shore-based IT support and emergency services
2.5 RECOVER – Test and refine your segmentation
You can’t shut down operations for extensive testing, but you can validate your segmentation during planned maintenance or crew changes.
Practical Testing Approach
- Simulated disconnection tests: Temporarily isolate vessel networks during port stays to ensure essential operations continue
- Backup system verification: Confirm backup communication and navigation systems work when primary networks are isolated
- Recovery time measurement: Time how long it takes to restore normal connectivity after isolation
Continuous Improvement
Network segmentation isn’t a one-time implementation. Schedule quarterly reviews to:
- Remove unnecessary connections that have been added
- Update segmentation based on new equipment or operational changes
- Refine procedures based on lessons learned from tests or actual incidents
3. Audit Readiness FAQ: What auditors actually look for
Q: Do I need to reinvent my entire Safety Management System for cyber compliance?
A: No. The IMO’s latest guidance reinforces Resolution MSC.428(98), which mandates that cyber risks be addressed in compliance with the International Safety Management (ISM) Code. You’re adding cyber risk management to existing SMS processes, not replacing them.
Q: What documentation do auditors want to see?
A: Three essential documents: 1) Network diagram showing segmentation between corporate and vessel systems, 2) Procedures for isolating vessel networks during cyber incidents, 3) Records of segmentation testing and incident response exercises.
Q: How do I prove compliance for vessels currently at sea?
A: Remote verification through network monitoring logs, communication records showing isolation capabilities, and crew interviews confirming understanding of procedures.
Q: What’s really different for small fleets versus major shipping lines?
A: Resource availability and technical support. Auditors understand SMB constraints and focus on whether you’ve implemented appropriate measures given your size and complexity, not whether you’ve matched enterprise-level security.
Q: How often do I need to test network segmentation?
A: Quarterly testing of isolation procedures is sufficient for most SMB operators. Document each test and any improvements made based on results.
4. The Business Case: Why network negmentation pays for itself
Immediate ROI
Proper network segmentation typically costs $2,000-5,000 per vessel to implement but can prevent incidents that average $550,000 in recovery costs. The ROI calculation is straightforward.
Operational Benefits
Beyond compliance, network segmentation provides:
- Improved system reliability through reduced interference between networks
- Faster troubleshooting when issues are contained to specific network segments
- Enhanced ability to prioritize critical operations during system problems
Competitive Advantage
Compliance gaps particularly challenge smaller operators, creating opportunities for operators who achieve effective compliance. Demonstrable cybersecurity compliance increasingly influences charter party negotiations and insurance rates.
5. Moving forward
IMO 2021 compliance doesn’t have to feel impossible. By focusing on network segmentation between corporate and vessel systems, SMB maritime operators can achieve meaningful compliance while building genuine operational resilience.
Start This Week : Begin with Step 1 of the segmentation starter kit: map your current network connections between corporate and vessel systems. This single action will provide clarity about your actual risk exposure and compliance gaps.
Build Systematically : Implement segmentation on one vessel first, document the process, and use lessons learned to accelerate fleet-wide deployment. This approach manages costs while demonstrating progress to auditors and stakeholders.
Focus on What Matters : Network segmentation addresses the primary attack vector affecting SMB maritime operators. Master this foundation before investing in additional cybersecurity measures.
Ready to Take Action?
The path to IMO 2021 compliance doesn’t require unlimited resources or technical expertise, it requires focus on the measures that actually prevent the incidents affecting SMB maritime operators.






